Featured
Table of Contents
- – Openvpn Vs Wireguard - What's The Difference ? ...
- – What Is Openvpn? Everything You Need To Know (...
- – What Is Openvpn? Everything You Need To Know (...
- – How Vpns Work, And Why You Need One On Your P...
- – Protocol State Fuzzing Of An Openvpn
- – What Is Openvpn Encryption? Why ...
- – Ipsec Vs. Openvpn—what Are The Differences?
- – Understanding Vpn Protocols: Openvpn, L2tp ...
Openvpn Vs Wireguard - What's The Difference ? (Pros ...
When you have actually set up the app on the devices, move on to step 5. Now you simply need to import the certificates and secrets already generated in the steps above. To do this, simply follow these actions: Copy the ca.
It is among the most safe procedures. If you opt for a third-party VPN service, it's suggested that you opt for a service provider that offers it in order to delight in a highly protected online experience without fear of hackers. We hope this guide addresses all concerns about how Open, VPN works, how to set it up and when you must utilize it.
The first thing to comprehend about Open, VPN is that it is a VPN procedure. A protocol is a set of guidelines that. It identifies how to secure and identify information packets passing across VPN connections.
What Is Openvpn? Everything You Need To Know (2023)

Open, VPN's open-source neighborhood checks bugs and refines the protocol, adding brand-new functions and upgrading security elements. Consistent examination suggests that the protocol is.
Open, VPN systems can serve a single workstation linking to a business network or scale approximately enterprise-wide security systems. The VPN is designed to cover as numerous devices as users require. Users download pre-configured customers, install them to their gadgets, and are all set to go. One of the biggest Open, VPN advantages is that users can set up Open, VPN customers on Windows, Linux, and mac, OS.
Users won't require to trust that corporations protect data and avoid security errors. A worldwide coding community fine-tunes Open, VPN to respond to the current cybersecurity patterns. The benefits noted above different Open, VPN from most other VPN protocols. No cybersecurity innovation is flawless. Open, VPN is no exception, and there are a number of potential weak points users need to understand about:.
What Is Openvpn? Everything You Need To Know (2023)
This is practical, but companies with bespoke security needs might discover other protocols more user-friendly. Open, VPN has become a streamlined option for desktop and laptop computer os however is not as slick for mobile users. Android and i, OS executions are not as advanced or user-friendly, although they are enhancing all the time.
However, due to the fact that UDP does not have a handshake process,. It is possible to lose information throughout transmission, making UDP less appropriate for service scenarios where precise transfers are all-important. Transmission Control Procedure (TCP) is the other Open, VPN mode. In this case, TCP is classified as a stateful procedure. This means that the server retains data about the session state.
You may believe Open, VPN is a type of VPN. What is Open, VPN? How does it work?
How Vpns Work, And Why You Need One On Your Phone
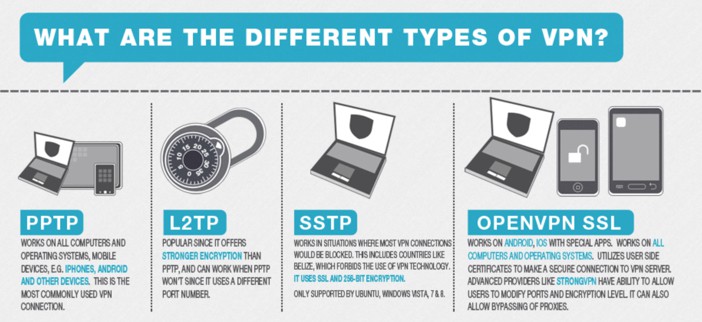
Point-to-Point Tunneling Protocol is a prime example. Stability is the calling card of others. Web Secret Exchange v2 is an excellent case in point. The most popular ones are extremely configurable for a range of usages - you can make them as secure and light-weight as the requirement occurs.
For example, Hotspot Guard counts on nothing but its exclusive Catapult Hydra. It utilized to support Open, VPN and IPSec (Internet Protocol Security), but Anchor, Free Inc. (its developer) felt both procedures had unacceptable latency issues. In time, brand-new tunneling protocols occur to take it up a notch. At the minute, Wire, Guard is the talk of the town.
The Open, VPN procedure can be a discomfort to set up by hand. Its intricacy, its only unassailable disadvantage, can make your head swim. TCP and UDP Open, VPN procedures are generally preconfigured in many VPN apps for personal use. Speaking of which, nearly all of the VPNs we have actually evaluated support Open, VPN.
Protocol State Fuzzing Of An Openvpn
Aside From Hotspot Shield, Hola VPN was the only other vendor we've come across that didn't use Open, VPN. Still, some of the most popular VPN services - like PIA, Surfshark, Nord, VPN, and Express, VPN - support it. Open, VPN is among the finest all-around VPN procedures out there.
Without a doubt, Open, VPN innovations are safe. It's no longer the very best at many things with the development of Wire, Guard. Open, VPN stays a decent choice for streaming, torrenting, and private web surfing.
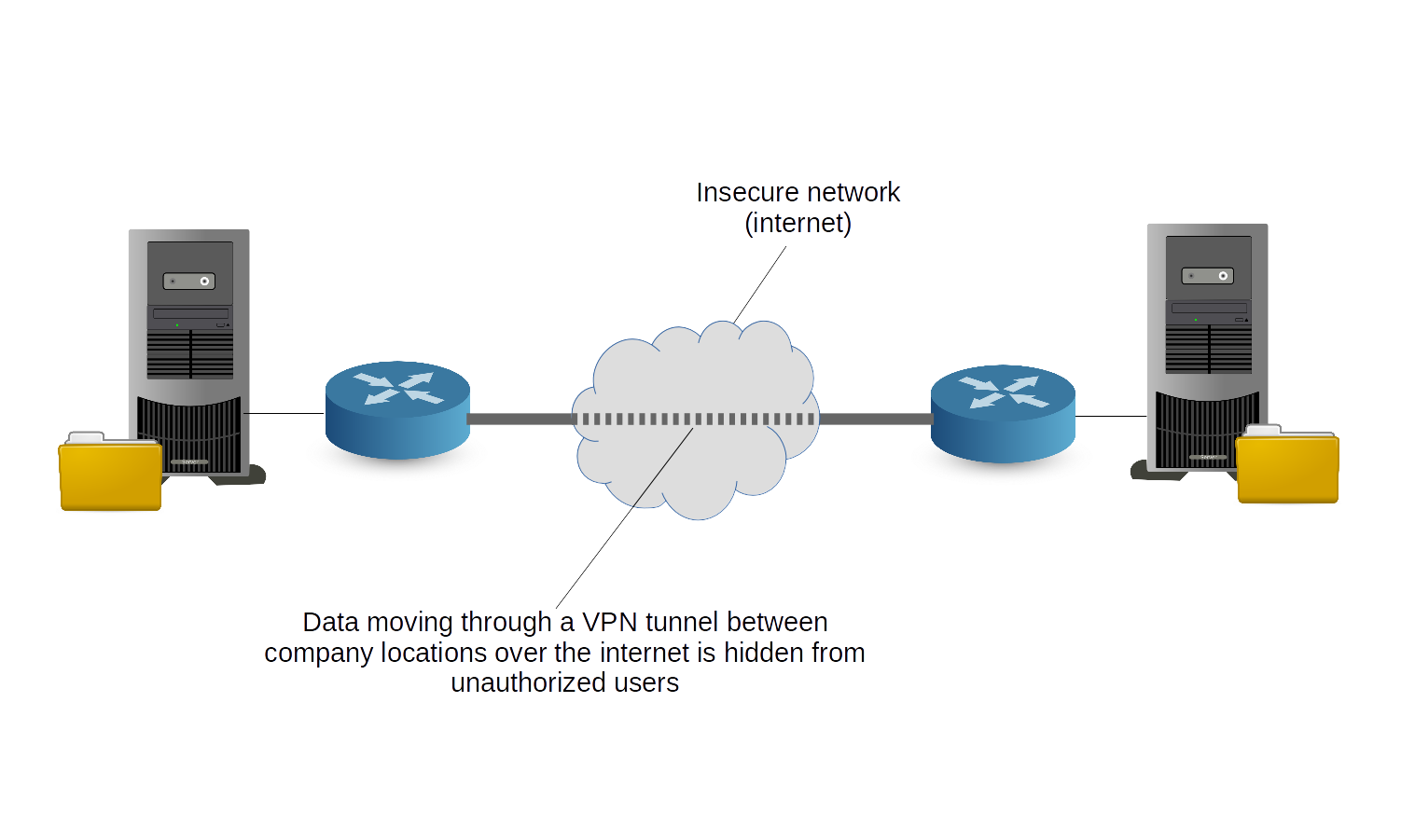
Over the past few years, Virtual Private Networks (VPNs) have actually ended up being an exceptionally popular method for protecting yourself while using the web. There's a range of VPN service providers out there, such as Nord, VPN, Surf, Shark, and Express, VPN, however you may not have become aware of the innovation they use.
What Is Openvpn Encryption? Why ...
Open, VPN is an open source connection protocol that uses encryption and authentication to produce a secure "tunnel" in between the user and the server. You may have heard popular VPN suppliers utilize this kind of example when explaining their service, and that's because many of them use Open, VPN to provide you with online security.
This is one of the Open, VPN's key security aspects, and stands as one of the most protected file encryption techniques out there today. On top of all this, Open, VPN is open source, suggesting that anybody can see the code, and that any bugs can be recognized and repaired quickly by the Open, VPN neighborhood if the designers do not see to it.
However how do you in fact utilize it? At this point, you may be thinking, "if Open, VPN is so excellent, why haven't I became aware of it prior to?". Well, Open, VPN is the innovation utilized by much of the top VPN suppliers you understand of, such as Browse, Shark, Personal, VPN, and Express VPN.
Ipsec Vs. Openvpn—what Are The Differences?
What many do not know is that Open, VPN, unlike the other providers mentioned above, is completely free to utilize, meaning you'll never ever need to handle any upfront charges or subscription charges. But can Open, VPN be utilized as quickly as popular providers just on its own? Related: How to Set Up a VPN in Windows 11 You can utilize Open, VPN personally, it is more geared towards services that have numerous people linking to a server at once.
This is another VPN procedure that can provide a more reliable connection and has a more safe kind of encryption. Only time will inform whether this protocol ends up being the next huge thing in online security. While it's simple to register for a subscription-based VPN service with simply a few clicks of the mouse, you may wish to consider giving Open, VPN a go if you desire the exact same innovation without an in advance or monthly charge.
To have the Open, VPN procedure described, we 'd say it's the most flexible of them all. Open, VPN Neighborhood Edition is the basic, complimentary variation of the software, while Open, VPN Gain Access To Server is the advanced, paid version.
Understanding Vpn Protocols: Openvpn, L2tp ...
One of the strengths of Open, VPN is that it can be used on both User Datagram Protocol (UDP) and Transmission Control Protocol (TCP). These are the communication standards that allow devices to exchange messages over the network. From what we have experienced, Open, VPN with TCP is more reliable, while Open, VPN with UDP appears to be faster.
Open, VPN is one of the safest VPN protocols on the market. The primary reason for that is that it's an open-source solution, and no company owns or runs it. You can be entirely sure your information is safely transmitted, and no one can get unauthorized access to it or offer it to a 3rd celebration.
Table of Contents
- – Openvpn Vs Wireguard - What's The Difference ? ...
- – What Is Openvpn? Everything You Need To Know (...
- – What Is Openvpn? Everything You Need To Know (...
- – How Vpns Work, And Why You Need One On Your P...
- – Protocol State Fuzzing Of An Openvpn
- – What Is Openvpn Encryption? Why ...
- – Ipsec Vs. Openvpn—what Are The Differences?
- – Understanding Vpn Protocols: Openvpn, L2tp ...
Latest Posts
Compare The Best Vpns For Work In 2023
3 Best Vpns To Use When Working Remotely For Your ...
The 6 Best Vpn Stocks To Buy Right Now For August 2023
More
Latest Posts
Compare The Best Vpns For Work In 2023
3 Best Vpns To Use When Working Remotely For Your ...
The 6 Best Vpn Stocks To Buy Right Now For August 2023